Demystifying Authentication: Exploring Passwords, Sessions, Cookies, Tokens, JWT, SSO, and OAuth
Introduction
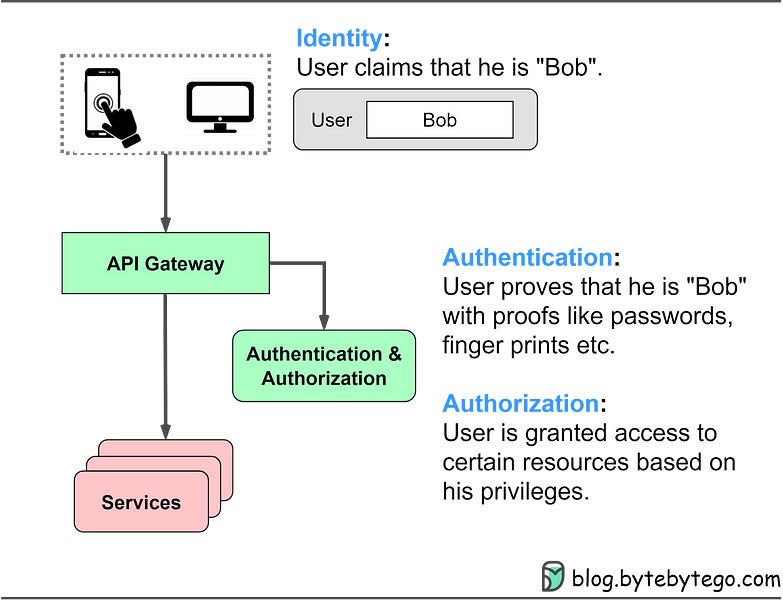
Authentication is a cornerstone of cybersecurity and user privacy. Understanding the various authentication methods and technologies is crucial for developers, security professionals, and anyone concerned with safeguarding digital identities. In this comprehensive guide, we'll unravel the intricacies of authentication, shedding light on passwords, sessions, cookies, tokens, JWT, SSO, and OAuth. By the end of this article, you'll have a clearer picture of how these mechanisms work together to ensure secure access to digital resources.
Password-Based Authentication
Passwords have long been the most common form of user authentication. Users provide a unique password during registration, which is then compared to the stored hashed password during subsequent logins. However, relying solely on passwords has limitations like vulnerability to brute-force attacks and users employing weak passwords.
Session Management and Cookies
Sessions play a vital role in maintaining a user's authentication state during their interaction with a web application. Cookies are used to store session identifiers in the user's browser. These identifiers allow the application to recognize users and grant access to authorized resources without the need for re-entering credentials with every request.
Tokens for Stateless Authentication
Tokens are the foundation of stateless authentication systems. When a user logs in, they receive a token that carries their identity and privileges. This token is sent with subsequent requests, removing the need for server-side sessions and enabling horizontal scalability.
JWT (JSON Web Tokens)
JWT is a compact, self-contained token format that's widely used for securely transmitting information between parties. It's commonly employed for authentication and authorization in web applications. JWTs consist of three parts: a header, a payload, and a signature, making them tamper-proof and easily verifiable.
Single Sign-On (SSO)
SSO simplifies user access across multiple applications by allowing users to authenticate once and then access various services without needing to re-enter credentials. It enhances user experience while reducing the risk of password fatigue and simplifying management.
OAuth: Enabling Third-Party Authentication
OAuth is a powerful protocol for granting third-party applications limited access to a user's resources without exposing their credentials. It's often used for scenarios like allowing apps to access a user's social media accounts or granting permissions to read specific email messages.
A Unified Approach: Balancing Security and User Experience
As the digital landscape evolves, combining these authentication methods and technologies becomes essential. Striking a balance between security and user experience ensures users can seamlessly and securely access the resources they need. By layering mechanisms like two-factor authentication (2FA) onto existing methods, an extra layer of protection can be added.
Conclusion: Navigating the Authentication Landscape
Authentication is the cornerstone of secure digital interactions, encompassing a range of methods and technologies. From traditional passwords to modern JWT and OAuth implementations, each mechanism plays a distinct role in ensuring the integrity and confidentiality of user data. As technology continues to advance, a comprehensive understanding of these authentication approaches will be essential for those committed to maintaining secure online environments.
By comprehending the intricacies of passwords, sessions, cookies, tokens, JWT, SSO, and OAuth, you're equipped with the knowledge to build robust, user-friendly authentication systems that elevate security while enhancing the user experience.
Chung Nguyen
